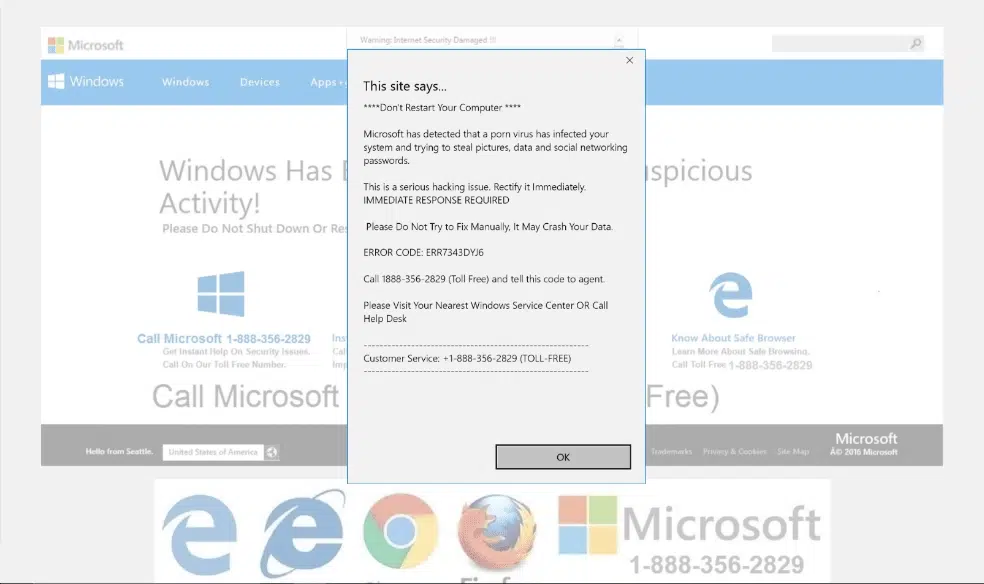
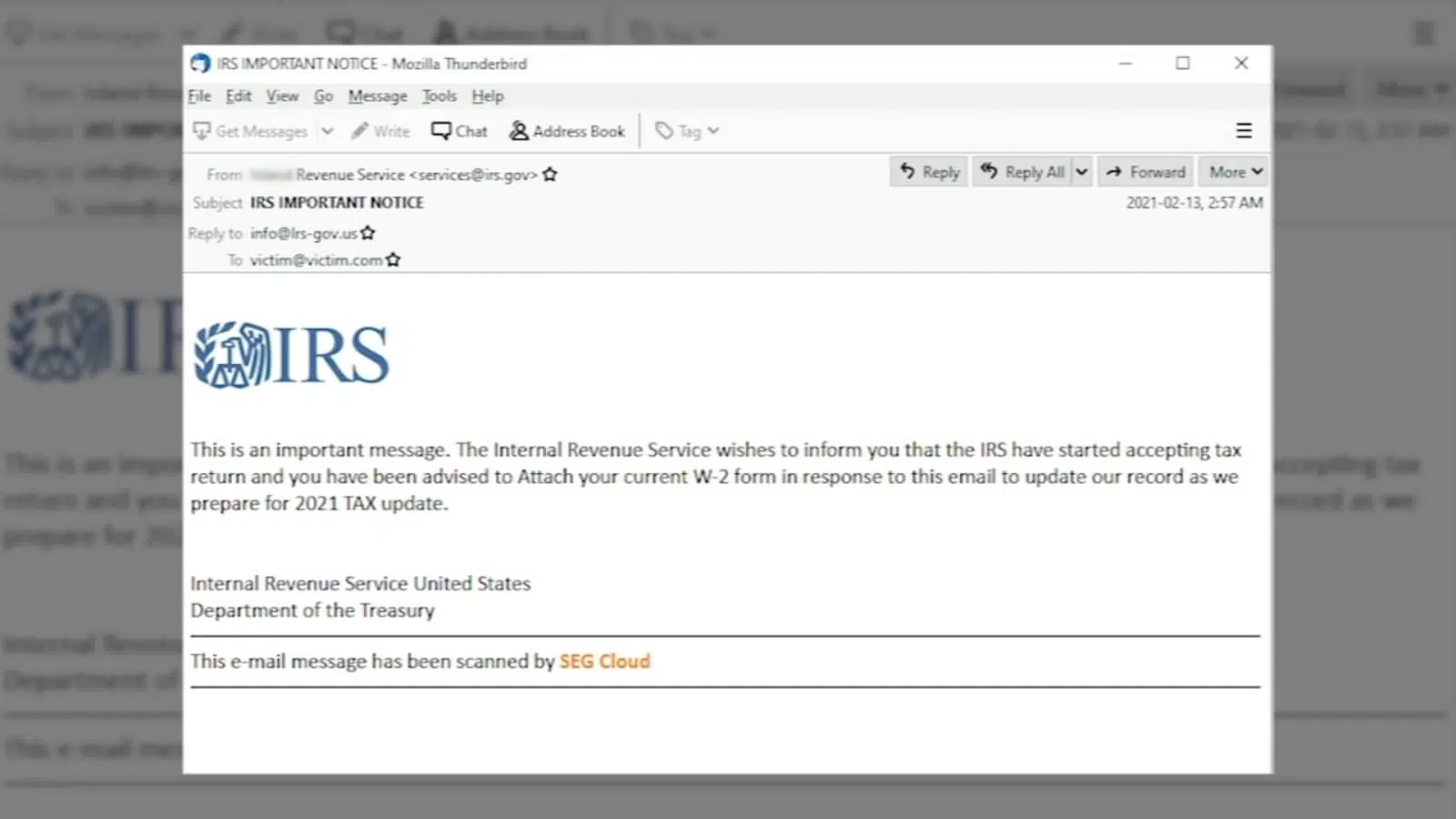
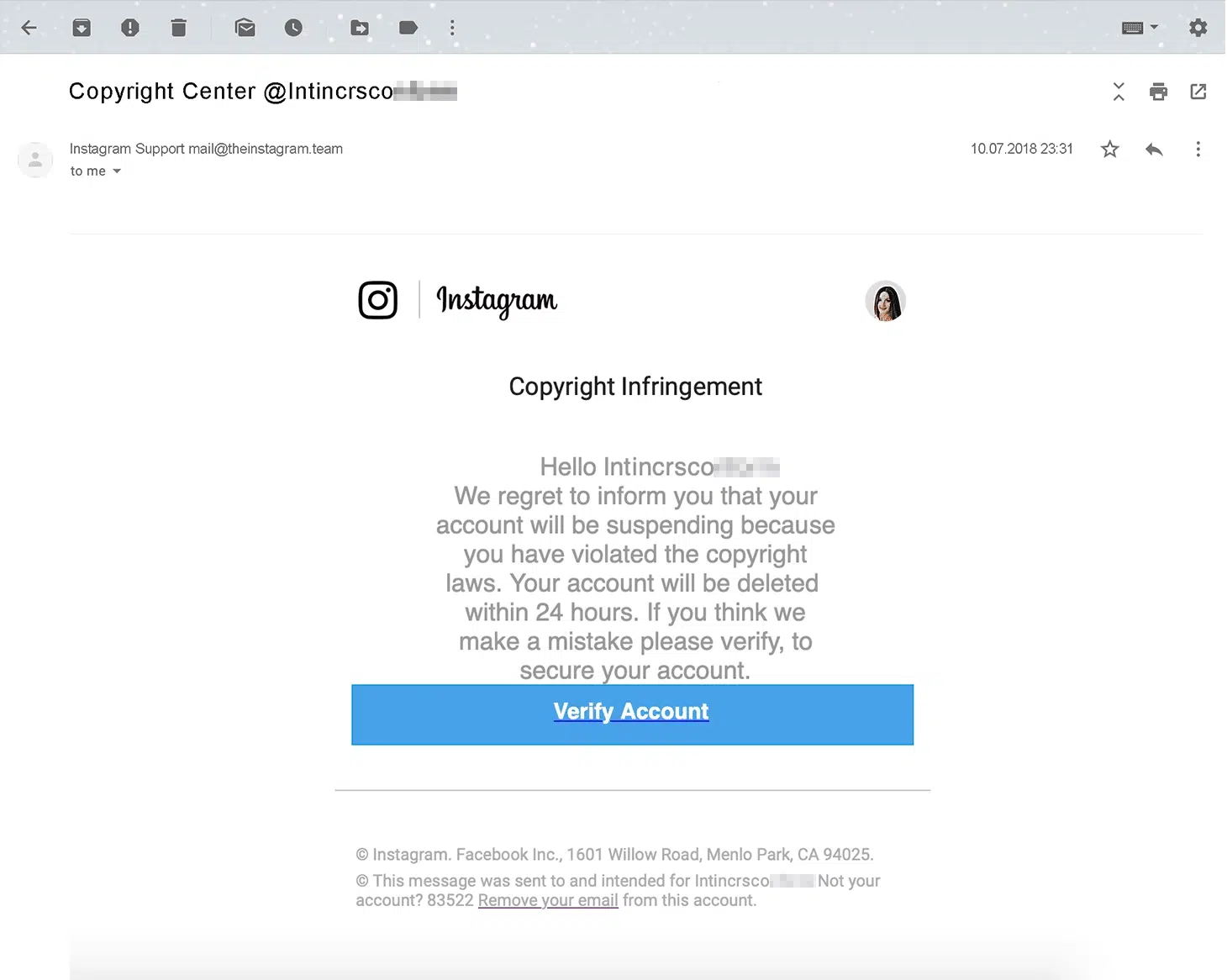
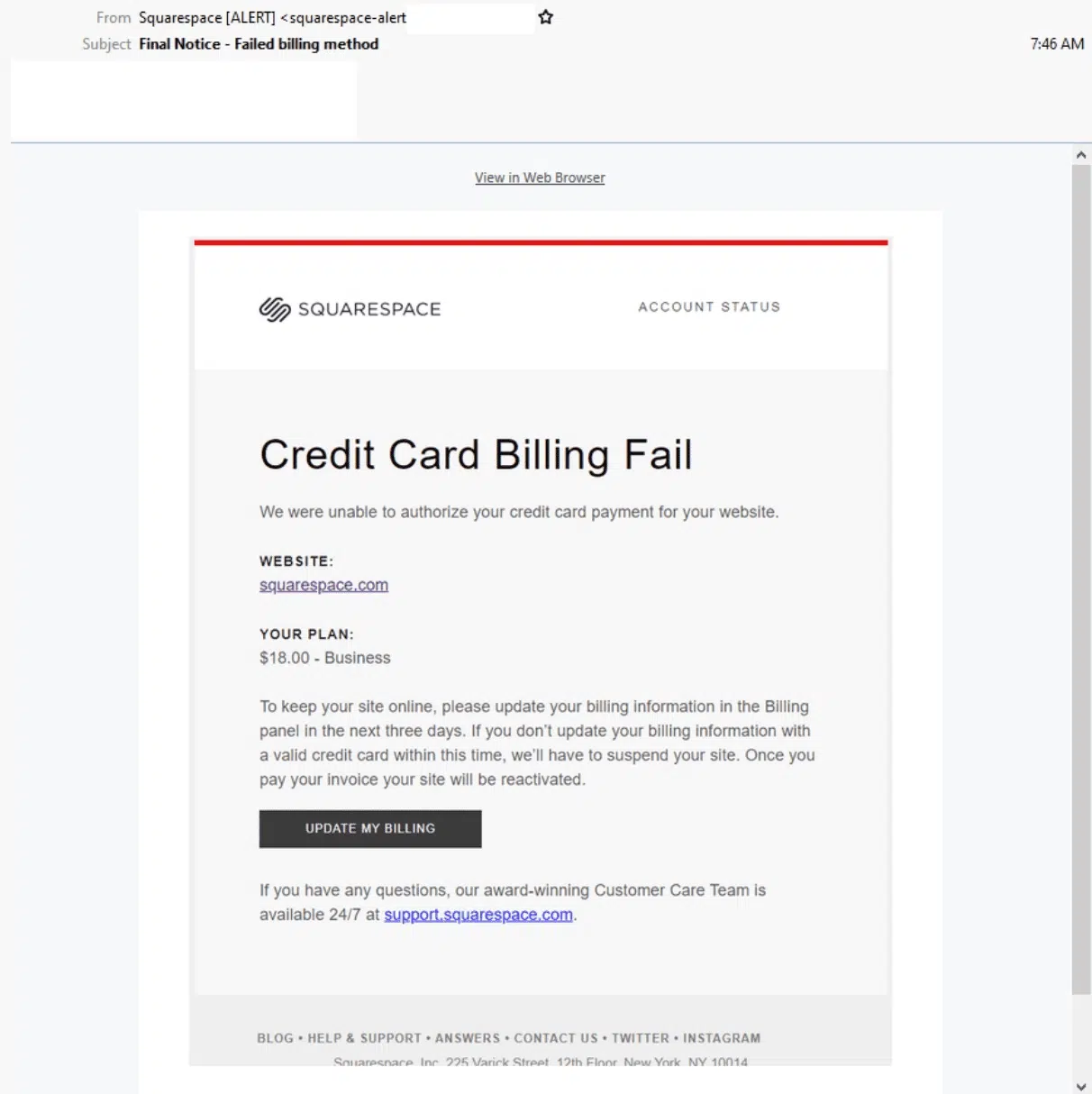
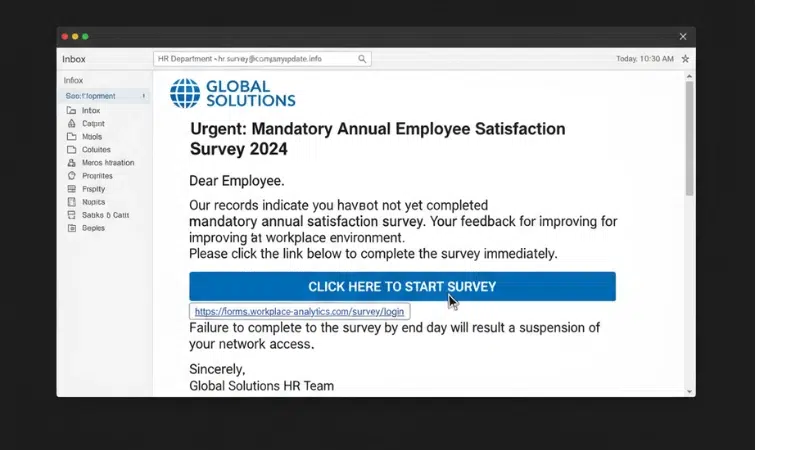
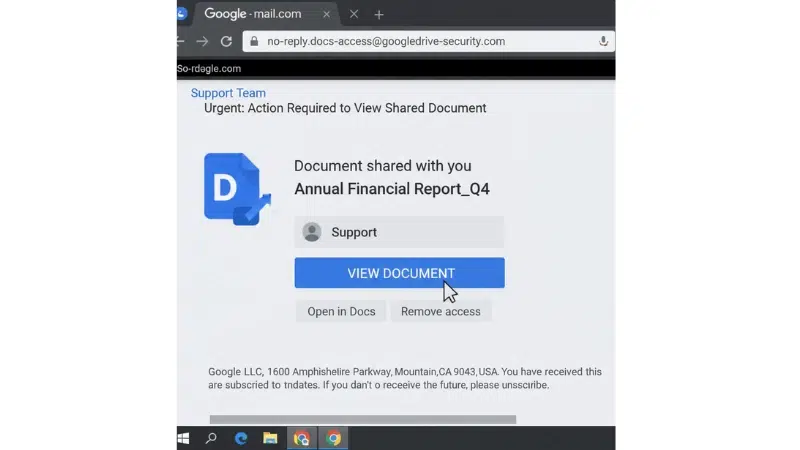
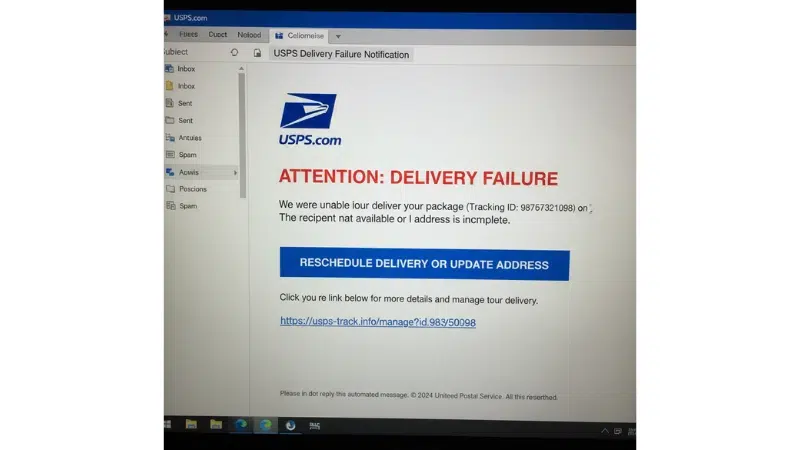
Email phishing is a major cyber threat that continues to affect many people today. Attackers often disguise themselves as trusted contacts and create a sense of urgency to trick individuals into sharing sensitive information.
The good news is that you can stop phishing attacks through awareness and effective tools. Always verify unexpected requests, use multi-factor authentication (MFA), and stay informed about prevention methods. For businesses, collaborating with professionals like Chipin Corp provides dependable IT support, Windows server support, and robust cybersecurity measures
A moment of caution can prevent significant harm. Stay vigilant, think before you click, and protect your digital presence.
For immediate IT support or queries, reach us on WhatsApp at +971529584840 or call us directly at +971 52 958 4840.